Blockchain, Bitcoin and distributed platforms
PART 1 – HASHES
Underneath the hype of the Bitcoin et. al being touted as an alternative currencies lurks some actual clever ideas and actual useful potential. I will attempt to highlight a few aspects of this type of technology and provide some insight into what useful technology may evolve from the current bitcoin/altcoin arena.
Hashes = proof
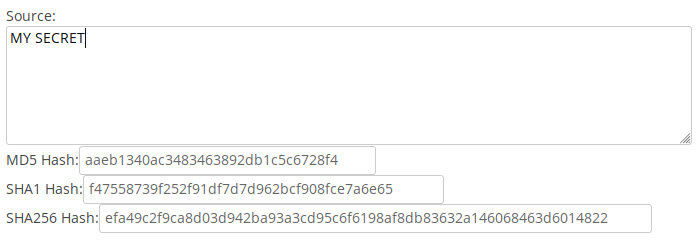
So what is a hash? It is the result of a chosen (cryptographic) computation technique performed on a given set of data. It can be easily reproduced using the same technique and data, but by design is very difficult to reverse engineer. Additionally, more that one set of data can produce the same hash although these collisions are likewise very difficult to produce. A single byte difference in the data typically results in a completely different hash result.
See my Hash Calculator Tool to see hash values being generated on-the-fly.
So Bitcoin and other blockchains for example, rely on these hashes as evidence that a computation has been done. Then that hash is combined with additional data and another hash value is then calculated for the next block in the sequence. So at any stage, previous blocks cannot be easily be falsified as it is so difficult to create false data that would produce the same hash.
Cryptographic Keys
Similarly, cryptographically generated ‘keys’ are used by such platforms that can be used to verify ‘ownership’ of blockchain accounts or addresses. By using special cryptographic techniques, it can be proved that someone holds a private key by giving a public key and a set of data, as the public key is enough to verify a transaction but not enough to recreate it. It is the equivalent of giving the fractional part of a number that can be verified 18128712847.12157126961 (.12157126961) while withholding the whole number part that is required to generate it (18128712847).
As evidence of how difficult it is to reverse engineer these private keys, there are several Bitcoin addresses that hold over a Billion dollars worth of Bitcoin. If they could be easily hacked, they would have been by now.
Multi-Party Cryptography Functions
Multi-party encryption techniques can be used to allow access to data when a certain number x of a total of y parties combine their keys. So keys can be shared between 3 parties but only 2 of the keys need to be combined to unlock the data.
Practical applications
So the blockchain/crypto era is bringing together several technologies that should be able to be used for practical purposes.
- Blockchains are fully auditable and auditable as previous data cannot be falsified
- Ownership of Data can be proven without the need to reveal the data itself
- Data can be selectively encrypted and decryption keys given to selected individuals
I will be looking into some practical applications in PART 2, coming soon.
